Easy way to protect your computer
The most effective and easy way to ensure your computer is safe. The tool we use to help you stay out of cyber troubles
In today’s world it’s more important than ever to keep your online and offline data safe and secure. That’s where the Protection Agent from Res-Q comes in. This software is designed to protect your computer from a failing hard drive, and to ensure that your computer is regularly updated and secured. In short, the Protection Agent ensures that your computer is updated, hardware checked and communications with the outside world are safe.
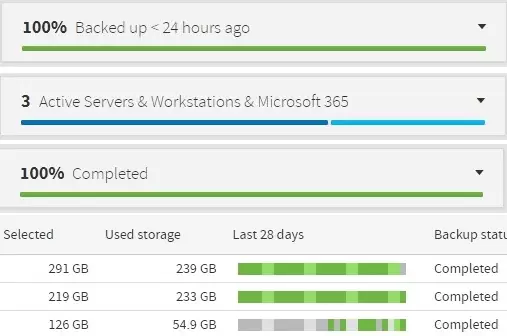
The Protection Agent monitors your computer for events that often go unnoticed. Additionally, the Protection Agent applies maintenance procedures and checks to see if backups (*) have been completed successfully
(*) backup monitoring is available as an option.
And if you ever run into an issue, the Protection Agent provides Res-Q engineers with answers that can help resolve the issue quickly.
What does the agent do to protect your computer?
Hardware Health Check
Windows operating system has 5 Windows Logs and 5 types of events recorded for every log every hour for almost 16,384 event sources. The only way to monitor and filter the critical events is via the Protection Agent.
When Protection agents detects an error it report back to a technician
Hackers and Crackers
There are good guys and the bad guys out there. The good guys are called Hackers. The hacker’s job, contrary to popular belief, is to find vulnerabilities in the software and report the issues to the software developers, such as Adobe, Microsoft, Java, MYOB etc.
The crackers are the bad people. They use vulnerabilities they discover to attack the systems, and to gain financial or other benefits. For example, scam you out of money.
That’s why it is extremely important to stay compliant. We make sure your Windows and other applications are up to date as soon as the patch (most recent update) is available.
Security and Online Protection
The universal rule is that every device that connects to the internet is exposed to online threats. Every individual could become a victim of a cyber criminal. Therefore, every device should be protected from different type of malicious threats.
The viruses that could infect your computer and encrypt documents are generally spread through the transmission of infected files.
The other danger comes from fileless viruses. For example, links to phishing or deceptive content (websites) that could result in you losing money to a scammer without you knowing until you check your bank statement
A single component, such as hard drive, or solid state drive, has more than 10 sensors detecting temperature, power failures, how many hours it was operating for and other critical data. We apply our knowledge and best practices from all around the world to ensure that critical events are reported to a technician and customer can make an informed decision to replace failing part and not rely on luck.
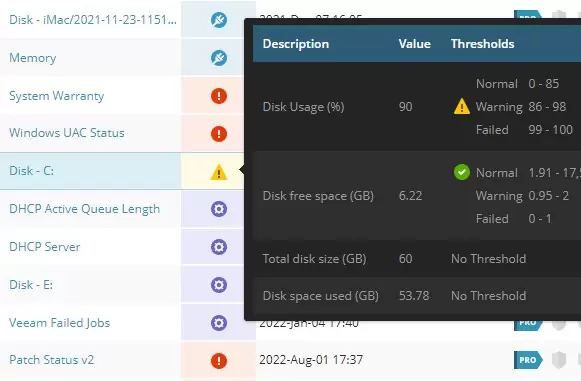
TIP: You can use a free tool such as Crystal Disk Report to determine if your hard drive is OK or needs to be replaced
Nick Shmakov
Can I buy an Antivirus only?
The simple answer is – yes you can.
Standalone antivirus software is only part of the solution to maintaining a healthy computer. You need to understand the warnings and problems identified by the software in order to take appropriate action. This can be difficult, as it is not always clear which alert is important and which can be ignored. As a result, many computers become infected and hard drives fail simply because warnings were not heeded. This can lead to disastrous consequences, such as the loss of important family photos. Only some can afford to have a dedicated computer professional to check and identify the state of your computer 24/7. That’s where the Protection Agent comes in.
The software checks for issues and raises the alarm 24/7. If there is a known solution the programme runs a set of commands that can heal the computer automatically. If the issue cannot be solved automatically the alarm reverts to a technician who can assess the matter and offer the client an appropriate actionable solution. If you believe that it is better to prevent such disasters you may opt in to have your the system health monitored by a Res-Q technician who can deal with emergent problems.
Finaly the DNS Filtering. The service that had become so important that we dedicated a number of articles to explain the basics of how it works and what it does. We want to ensure there is no chance left to luck when you click while surfing internet.
Would you like to know more?
5 ways to protect your privacy online Share on facebook...
5 steps to get great wifi in every corner of...
5 ways to improve wifi coverage at home or office...